
Do you feel attached to the (virtual) things in your smartphone?
你對智慧手機裡的虛擬物件有情感連結嗎?
Project overview
Virtual
possession
attachment
the emotional relationship between individuals and their virtual possessions.
人與其虛擬擁有物之間的情感關係
This research explores emotional relationship between individual and their virtual possessions by Grounded Theory. We conducted 24 in-depth interviews with younger adults (under 20- year-old) and elder adults (above 40-year-old) in Taiwan. By understanding usage behaviors and feelings about participants’ important virtual possessions, several findings came out. The findings are presented as materials for building a theory of attachment development to virtual possessions.
The Challenge
Understand the emotional relationship, including context and possibilities, between human and virtual possessions.
My Role
The research had mostly done by me. However, I definitely could not finish it without my advisors, my code team and all the people who had helped me on it. I spent about a year developing the research questions. I had talked to many professionals in different domains and got various suggestions. Also, reading lots of related reference helped me understand the progress of recent studies. Those methods made me think wider and deeper to the phenomenon I observed. Eventually, I came up the research context myself and searched for the adaptable methods that could help me answer my research questions.
background
01
What is product attachment?
Attachment theory was first proposed by Bowlby in 1979 describing an emotional-laden target-specific bond between two persons. Furthermore, it has been applied to the relationship between human and object. This opens a novel perspective toward how we interact with our objects. In this regard, the interaction between an individual and his/her objects has not only involved functionality but also the perception and the entire context.
02
Why do we attach to a product?
Belk (1988) proposed that people consciously or unconsciously extend their selves to their possessions. He organized a big amount of relevant researches and claimed that self-extension is the reason why people attach to their possessions.
“Knowingly or unknowingly, intentionally or unintentionally, we regard our possessions as parts of ourselves” (139) (Belk, 1989)
Do the attachment exists between human and virtual possessions?
Belk (2013), who had proposed that self-extension is the reason for us to attach to possessions, addressed several changes of self-extension to virtual possessions by organizing recent researches. He indicated the according to the recent researchers, self-extension between individual and their virtual possessions indeed exist. Yet there are still some different between them and self-extension to physical possessions.
03

We are surrounded by an enormous amount of objects in everyday life. The notion of human-object relationship has been more and more complicated through the development of technology. To date, people have increasingly acquired virtual objects in their daily life. Researchers recently focus on the concept of how people develop emotional relationship to their digital object. However, there is still an open question that how and why people attach to their virtual possessions and what are the characteristics of the attachment.
Research Question
RQ1. What leads to attachment to virtual possessions and how it developed?
RQ2. What are the characteristics of attachment to virtual possessions?
data collection

First, interview protocol was prepared and conducted with 5 pilot interviews. Few details were slightly modified and 24 formal interviews were following proceeded. After data collection, based on Grounded Theory coding approach (Glaser & Strauss, 2009), three stages of coding procedure were done. In open coding, a code team (consisted of 3 graduate students and author) coded the 24 transcripts into conceptual labels and classified into 38 categories step by step.
Moreover, during the process, constant comparisons had been done for possibly catching everything. After the 38 categories were approximately confirmed, relationships between categories were coded by author. Furthermore, three core categories were selected and a storyline were drawn for the preliminary concept of theory building.
Since the data are huge and complicated, following I will introduce the method in five main procedures. References are available upon request.
01Interviewee sampling
Gender
and age
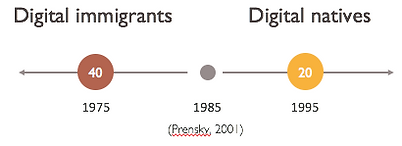
According to literature review in the previous section, data was collected by 24 interviews with younger adults (13-20 years old) and elder adults (40-51 years old) in Taiwan. In addition, participants are requested to have at least one important virtual possession such as digital photo, music, text messages, files and software, even the Facebook account.
In addition, according to previous studies of self-extension and attachment to possessions (Belk, 1988; Kleine et al., 1995), men and women extend to possessions differently. Hence, we tried to make the tender of participants as equal as possible.
Online Questionnaire
All the participants were recruited from the Internet with a poster. Not everyone who signed up for the interview was ultimately selected for the participant. People were asked to fill a prescreen questionnaire in advance in order to make sure their conditions are fit in this study.
There are three main purposes of the prescreen questionnaire: information for participant’s most important virtual possession, usage habit of digital device and personal contact information. Table 3.1 shows the questions in questionnaire and the justification of them.
Eventually, twenty-four participants were selected from the prescreen questionnaires. They were following sent an email, inviting them to schedule a time for an in person interview with the researcher. Every participant was offered 300NTD and a MUJI notebook for incentive.


02Interview protocol

A tentative interview protocol was design for 5 pilot interviews. Several problems were modulated and a primary protocol emerged for 24 formal interviews. During the interview process, protocol was iteratively modified according to the previous one.
To develop further research questions as interview questions, the justification of the research questions is required. The research questions have been deconstructed into several secondary-questions in order to specific in the interviews. The secondary-questions were designed based on the literature and pilot study.
The secondary-research questions were classified into three categories: usage behavior, feelings and personal value. Questions of understanding participants’ mindset were added in order to further understand the deeper reasons of usage behavior and feeling.
03Interviewing


All the twenty-four interviews were audio recorded and transcribed. Field notes and photos were taken when necessary during the interview.
Participant could choose the preferred interview place as long as it is quiet enough for audio recording. Thus, most of the interviews were conducted in public café or restaurant. Few of them were hold in participants’ home and work place.
03Card-sorting task before interview

According to the pilot interview, we found it is not easy for participant to realize the concept of “virtual possessions.” Some elder adult cannot easily answer the question about “digital possessions (Cushing, 2012)
(1) Help the participant adapt to the concept of “attachment to virtual possessions.”
(2) Understand the emotional relationship of participant and their virtual possessions
roughly before interviewing.
I referred Q method while designing the card-sorting task. Q method usually used to elicit individual’s viewpoints by card sorting. The sorting task was hold in before every interview.
I was taking notes and watching beside in order to answer all the questions that participants might have with the statements.

The interviews were conducted in semi-structure. Thus, interviewer could adjust the questions and their sequence depending on different conditions. Each interview was hold approximately 1.5 to 2 hours including the card-sorting task. Participants are encouraged to bring and share their virtual possessions while answering the questions.
data analysis

All the vocal data from interview were transferred into transcripts in order to be analyzed by coders.
All of the transcripts and filed notes were analyzed by open coding, axial coding and selective coding. The three stages of coding is conducted for extracting the core categories of relationship between participants an their virtual possessions.
01Find the categories: Open Coding

For a better reliability, a code team was established in the stage of open coding. All of the data were reviewed and discussed by coders repeatedly so as to prevent the viewpoints from over-subjective.
There are four coders in the team consisted of three graduate students and the author. All of the coders are from Department of Industrial Design in Cheng Kung University but with the different background, including Engineering, Phycology, Literature and design.
02Fine the relationship: Axial Coding and Selective Coding
In axial coding, the researcher has to connect categories into one key element, called “in vivo concepts” (Strauss & Corbin, 1990), which contain the researcher’s thoughts and ideas, and the concepts also have their own dimensions and properties.
After axial coding, several main categories were emerged. Based on the research question, the core category - the attachment development of virtual possessions was formed and some categories were united and developed into a storyline.

findings
As a qualitative research, there are a great quantity of findings and their meanings. Following I will briefly introduce the categories of the findings. However, the interesting and detail findings which need to be support with data and reference would not be presented here (also due to the copyright). Still, references are available upon request.


acknowledgement
<The different attachment to virtual possession between younger and elder adults> had been selected in 2016 HCII Conference. I would like to express my sincere gratitude to my thesis advisor, Professor Yuan-Chi Tseng and my committee members, Prof. Hao-Chuan Wang, Prof. Jones Yu, Prof. RungHuei Liang, Prof. Wen Lin and Prof. Yung-Ju Chang.